Bypassing ColdFusion and Lucees Global Script Protection When Designing a Content Management System
|
Apr 2 |
ColdFusion and Lucees Global Script Protection are designed to discourage cross-site scripting attacks by replacing scripts and other potentially harmful tags in forms before sending the data to the server. However, sometimes, this can get in the way—especially when trying to develop a content management system. In this article, I will show you various methods to bypass this security feature.
Table of Contents
What is ColdFusion and Lucee's Global Script Protection?
ColdFusion and Lucee's Global Script Protection is a security feature designed to prevent the injection of potentially harmful scripts on the server. This feature eliminates one of the common vectors used in cross-site scripting attacks.
Global Script Protection removes certain objects, such as scripts, styles, and applets, among other potentially dangerous stuff, and replaces these objects with an 'InvalidTag' before server-side processing occurs.
This sanitation occurs when input is sent to the server via a form, AJAX, or a header. This is an important security feature; however, it poses problems when the site administrator uses interfaces that require the input of these scripts, such as when designing a content management system.
How do you bypass ColdFusion and Lucee's Global Script Protection?
Site administrators may bypass Global Script Protection globally on the server, on a per-application basis, or programmatically.
Bypassing Global Script Protection on the Server
ColdFusion and Lucee allow you to use the administrator to turn off Global Script Protection. However, this is not recommended as it will turn off this security feature globally. While Global Script Protection does not guarantee your code's security, it effectively removes one of the most commonly used vectors for cross-site scripting attacks.
Modifying ColdFusion and Lucee's Global Script Protection Behavior
ColdFusion
You may modify the behavior of ColdFusion's Global Script Protection by editing the neo-security.xml located in WEB-INF/cfusion/lib. You should back this file up before editing if something goes awry and you need to back out of any changes. The default settings below will replace any object, embed, script, applet, or meta strings with 'InvalidTag'.
neo-security.xml:
<var name="CrossSiteScriptPatterns">
<struct type="coldfusion.server.ConfigMap">
<var name="<s*(object|embed|script|applet|meta)">
<string><InvalidTag</string>
</var>
</struct>
</var>Lucee
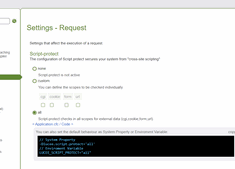
Lucee exposes these settings in the Lucee Administrator where you can specify the protected scopes. The available scopes in Lucee are: CGI, cookie, form and URL. It should be noted that Lucee also prohibits iframes and will replace them with InvalidTag as well.
Modifying Global Script Protection Per Application Basis
You may override Global Script Protection on the application level by setting this.scriptprotect to none in the application.cfc template like so:
this.scriptProtect="none"This behaves identically with ColdFusion and Lucee.
Programatically Bypassing Global Script Protection
In Galaxie Blog, I bypassed Global Script Protection programmatically because certain hosting providers would not allow you to turn it off. This approach takes a little more work; however, I like that it requires deliberate intention while keeping the original script protection features on. It is nice to also have the added security of Global Script Protection for other features, such as protecting against cross-site scripting when users make comments.
My methodology is to modify the potential tags that Global Script would remove before hitting the server and then replace these faux tags with the correct tags when saving the data to the database.
Client Side Logic
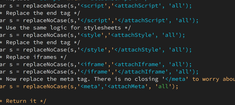
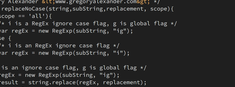
To perform this, I use the following JavaScript on the client side before sending the request to the server. Note that the replaceNoCase function on the client is a JavaScript function replicating the functionality of ColdFusion and Lucee's replaceNoCase.
Note: I am using images here to display the client side JavaScript , otherwise the server-side code will revert the 'attachX' strings back to the intended client-side code.
The actual JavaScript source code can also be found at: https://www.gregoryalexander.com/blog/test/gsp/testScript.cfm
Server-Side Logic
The following logic is on the server before saving the data to the database. If you wish, you can also use the same script to revert the strings back to the original before delivering the content back to the client.
<cffunction name="sanitizeScriptProtection" access="public" output="true" returntype="string"
hint="Cleans up the 'attach' strings to bypass script protection">
<cfargument name="s" type="string" required="yes">
<!--- Clean up 'script' --->
<cfset s = replaceNoCase(s, "script", "script", "all")>
<!--- ...'style'... --->
<cfset s = replaceNoCase(s, "style", "style", "all")>
<!--- ...'meta'... --->
<cfset s = replaceNoCase(s, "meta", "meta", "all")>
<!--- Return it --->
<cfreturn s>
</cffunction>Further Reading
Tags
Global Script Protection, Lucee, ColdFusion|
|
Gregory Alexander |
|
Hi, my name is Gregory! I have several degrees in computer graphics and multimedia authoring, and I have been developing enterprise web applications for the last 25 years. I love web technologies and the outdoors and am passionate about giving back to the community. |
|
This entry was posted on April 2, 2025 at 8:43 PM and has received 4020 views.
Comments
There are 5 comments.
Show Comments| #1 by Gregory Alexander on April 4, 2025 at 9:28 PM |
|
|
| #2 by James Moberg on April 4, 2025 at 9:16 PM |
|
I still don't see the difference between " |
| #3 by Gregory Alexander on April 4, 2025 at 9:08 PM |
|
|
| #4 by Gregory Alexander on April 4, 2025 at 9:00 PM |
|
|
| #5 by James Moberg on April 4, 2025 at 4:42 PM |
|
Also, have you ever encountered any odd CF errors when using replaceNoCase on large text strings? We did & reported it. I'm not sure if it ever got fixed, but we've been using java's replaceAll() on strings w/"?i" case-insensitive mode and have never encountered the error again. I've injected "x" to the strings to avoid using entities and make it more unique for replacement purposes. replaceAll("(?i)\ We encountered similar security hurdles when using WAF-protected web applications. It didn't matter what the Application.cfc's "scriptProtect" was set to and false positives were causing issues too. To circumvent this, we used JavaScript to convert the entire form payload to JSON, HEX encode it, post it as single, specially named form variable and then decode it on the server to recreate all FORM params. (NOTE: "File" input types weren't converted to JSON and were retained when passed in the POST request. All potentially sensitive inputs were set to "disabled" prior to the form submission so they wouldn't be included.) |